Application Layer Protocols: Interview Notes
1. Overview of Application Layer Protocols
What is it? Top layer (Layer 7) of OSI/TCP-IP model. Enables end-user applications (e.g., browsers, email clients) to communicate over a network.
- Key Protocols:
- HTTP/HTTPS: Web browsing
- FTP: File transfers
- DNS: Domain to IP resolution
- DHCP: Dynamic IP assignment
- SMTP/POP3/IMAP: Email communication
2. HTTP vs HTTPS
HTTP (HyperText Transfer Protocol)
- Purpose: Transfers web resources (e.g., HTML, images) between client and server.
- Port: 80
- Key Points:
- Stateless: Each request is independent.
- Plain text: Data unencrypted, vulnerable to interception.
- Example:
GET /index.html HTTP/1.1fetches a webpage.
- Use Case: Non-sensitive websites (e.g., static blogs).
HTTPS (HTTP Secure)
- Purpose: Secure HTTP using SSL/TLS encryption.
- Port: 443
- Key Points:
- Encrypts for confidentiality, integrity, authentication.
- SSL/TLS handshake:
- Client sends supported protocols.
- Server responds with certificate (public key).
- Symmetric key established.
- Trusted by Certificate Authorities (CAs).
- Use Case: Secure sites (e.g., banking, e-commerce).
- Example: Accessing
https://www.amazon.com.
HTTP vs HTTPS
| Feature | HTTP | HTTPS |
|---|---|---|
| Security | Unencrypted | Encrypted (SSL/TLS) |
| Port | 80 | 443 |
| Performance | Faster (no overhead) | Slower (encryption) |
| SEO | No benefit | Boosts ranking |
| Trust | No padlock | Padlock in browser |
- Key Phrase: “HTTPS ensures secure communication using SSL/TLS, critical for sensitive data.”
- Common Question: Why HTTPS? (Answer: Security, SEO, trust).
- Stand Out: Mention browsers marking HTTP as “Not Secure” and CA verification.
3. HTTP Methods
Definition: HTTP verbs specify client actions on server resources. Used in RESTful APIs for CRUD operations.
Key Methods
- GET:
- Purpose: Retrieve a resource.
- Traits: Safe, idempotent.
- Example:
GET /api/users/123fetches user data. - Use Case: Viewing webpages, API data retrieval.
- POST:
- Purpose: Create/update a resource.
- Traits: Not idempotent.
- Example:
POST /api/userswith{ "name": "John" }. - Use Case: Form submissions, file uploads.
- PUT:
- Purpose: Update/create a resource at a specific URL.
- Traits: Idempotent.
- Example:
PUT /api/users/123updates user details. - Use Case: Updating profiles.
- DELETE:
- Purpose: Remove a resource.
- Traits: Idempotent.
- Example:
DELETE /api/users/123deletes a user. - Use Case: Removing records.
Other Methods
- PATCH: Partial updates (e.g.,
{ "email": "new@example.com" }). - HEAD: Retrieves headers only.
- OPTIONS: Lists allowed methods.
- Key Phrase: “GET and DELETE are idempotent and safe; POST is neither.”
- Common Question: GET vs POST? (Answer: GET retrieves via URL; POST creates via body).
- Stand Out: Relate to REST APIs.
4. HTTP Status Codes
Definition: Three-digit codes indicating HTTP request results (1xx: Informational, 2xx: Success, 3xx: Redirection, 4xx: Client Error, 5xx: Server Error).
Key Status Codes
- 2xx (Success):
- 200 OK: Request succeeded.
- 201 Created: Resource created.
- 204 No Content: Success, no body.
- 3xx (Redirection):
- 301 Moved Permanently: Resource moved.
- 302 Found: Temporary redirect.
- 304 Not Modified: Resource unchanged.
- 4xx (Client Error):
- 400 Bad Request: Invalid syntax.
- 401 Unauthorized: Authentication required.
- 403 Forbidden: Access denied.
- 404 Not Found: Resource missing.
- 429 Too Many Requests: Rate limit hit.
- 5xx (Server Error):
- 500 Internal Server Error: Generic issue.
- 502 Bad Gateway: Invalid upstream response.
- 503 Service Unavailable: Server down.
- Key Phrase: “4xx for client errors; 5xx for server errors.”
- Common Question: 401 vs 403? (Answer: 401 needs login; 403 denies access).
- Stand Out: Give examples (e.g., 404 for missing page).
5. FTP – File Transfer Protocol
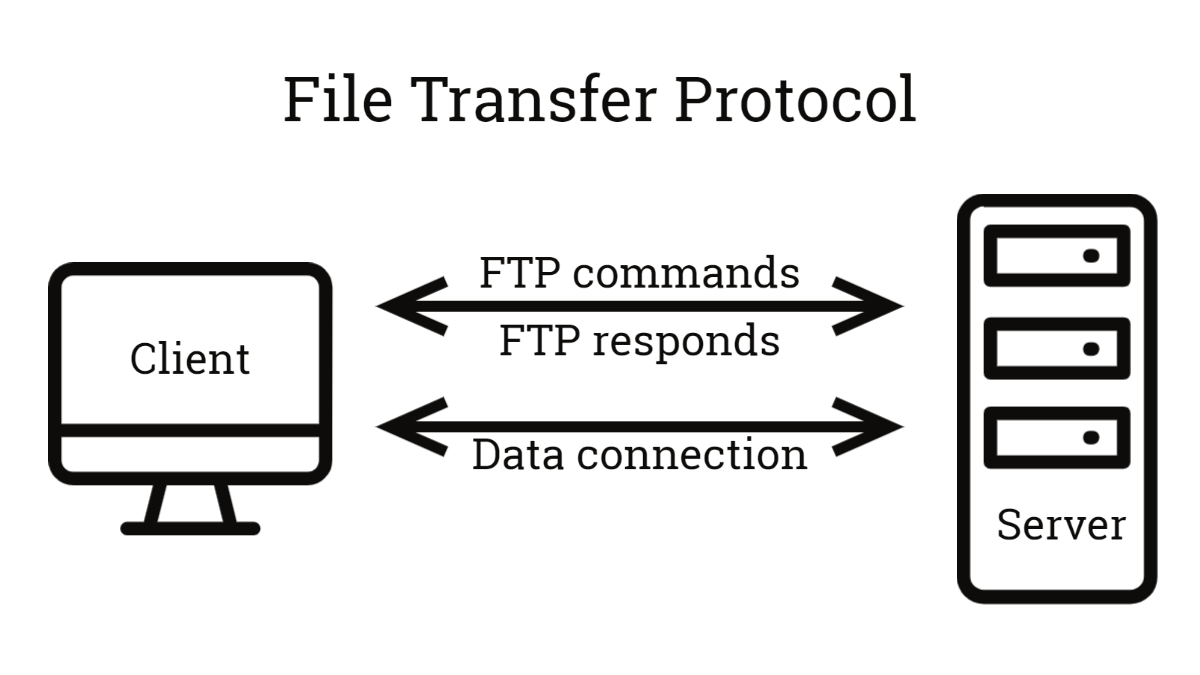
- Purpose: Transfers files between client and server.
- Port: 21 (control), 20 (data, active mode).
- Modes:
- Active: Server initiates data connection.
- Passive: Client initiates (firewall-friendly).
- Commands:
GET(download),PUT(upload),LIST(directory),DELE(delete). - Security: Unencrypted, vulnerable.
- Secure Alternatives:
- FTPS: FTP with SSL/TLS (ports 989/990).
- SFTP: File transfer over SSH (port 22).
- Use Case: Uploading website files, backups.
- Key Phrase: “FTP is insecure; SFTP is preferred for secure transfers.”
- Common Question: FTP vs SFTP? (Answer: FTP is plain text; SFTP uses SSH).
- Stand Out: Mention alternatives like AWS S3 or SCP.
6. DNS – Domain Name System

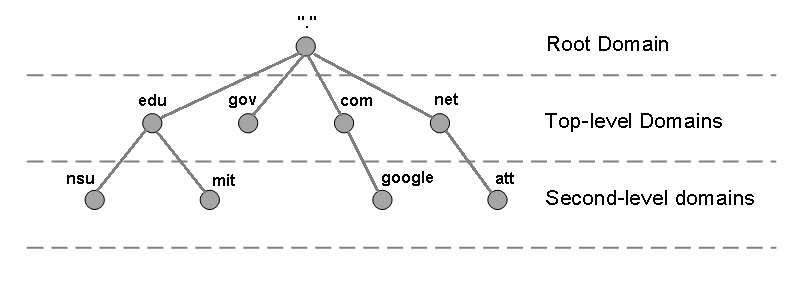
- Purpose: Translates domains (e.g.,
www.google.com) to IPs (e.g.,142.250.190.78). - Name Resolution Process:
- Client queries URL.
- Checks cache or hosts file.
- Recursive resolver queries root servers.
- TLD servers direct to authoritative server.
- Authoritative server returns IP.
- Resolver caches and sends IP to client.
- Port: UDP 53 (queries), TCP 53 (large responses).
- Record Types:
- A: IPv4 address.
- AAAA: IPv6 address.
- CNAME: Alias.
- MX: Mail server.
- NS: Name server.
- Security: Vulnerable to spoofing; DNSSEC adds authentication.
- Caching: Speeds up queries.
- Key Phrase: “DNS resolves domains to IPs.”
- Common Question: Explain DNS resolution. (Answer: Cache to authoritative server).
- Stand Out: Mention tools like
nslookupordig, and DNSSEC.
7. DHCP – Dynamic Host Configuration Protocol

- Purpose: Assigns IP addresses and network settings dynamically.
- DORA Process:
- Discover: Client broadcasts
DHCPDISCOVER. - Offer: Server sends
DHCPOFFER(IP, subnet, gateway). - Request: Client sends
DHCPREQUEST. - Acknowledge: Server sends
DHCPACK.
- Discover: Client broadcasts
- Port: UDP 67 (server), 68 (client).
- Lease: Temporary IP assignment.
- Parameters: IP, subnet mask, gateway, DNS servers.
- Use Case: Wi-Fi networks, office LANs.
- Key Phrase: “DHCP automates IP assignment via DORA.”
- Common Question: What if DHCP fails? (Answer: APIPA or no connection).
- Stand Out: Mention IP conflicts, lease renewal.
8. Email Protocols – SMTP, POP3, IMAP (use UDP or TCP)
SMTP – Simple Mail Transfer Protocol
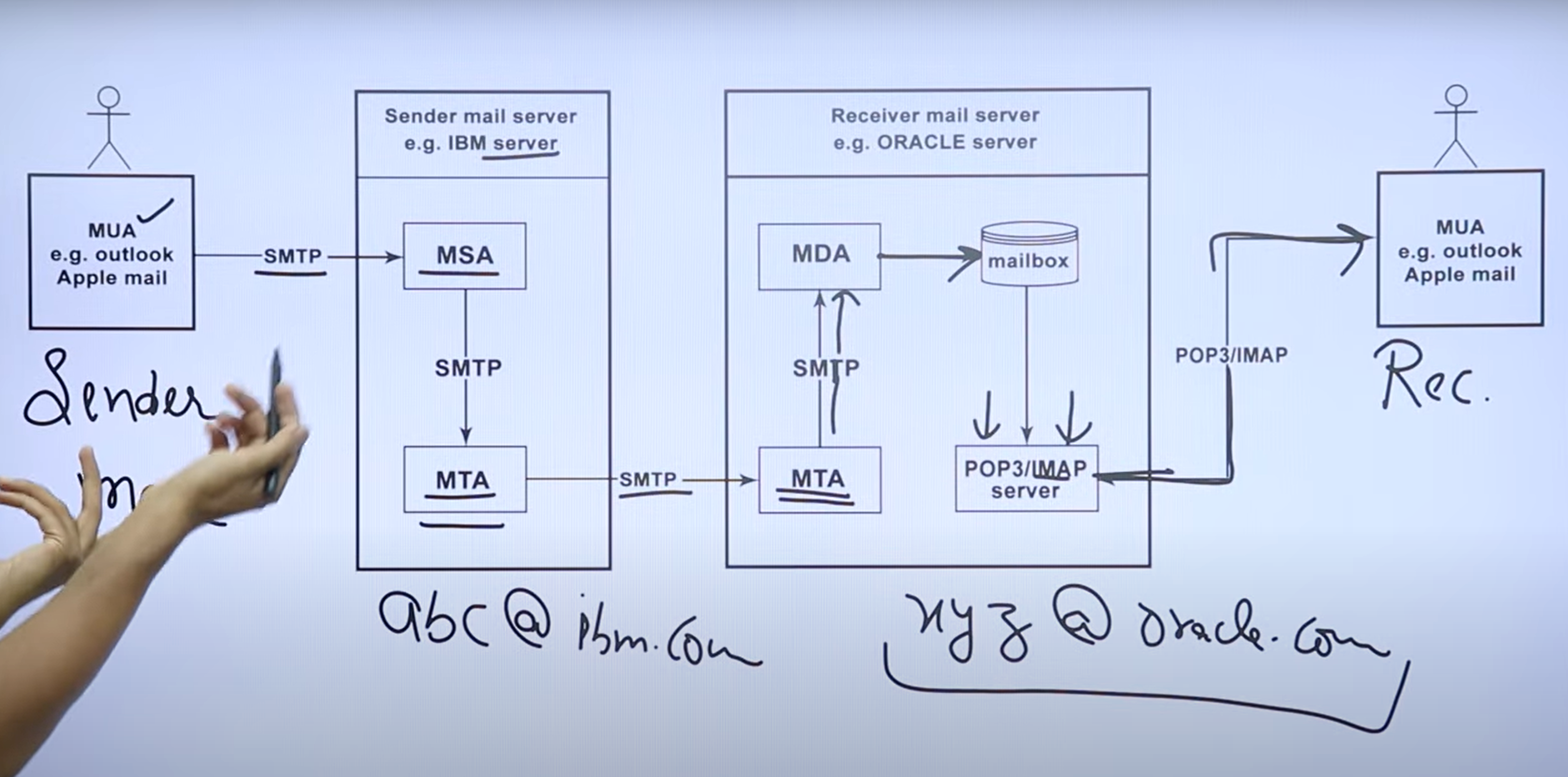
- Main job: Push (send) emails from you to someone else.
- Ports: 25 (basic), 587 (secure), 465 (secure).
- Example: You click "Send" in Gmail → Email goes to your friend.
POP3 – Post Office Protocol, Version 3
- Main job: Download emails from the server to your device.
- What happens: After download, emails are usually removed from the server (stay only on your device).
- Ports: 110 (basic), 995 (secure).
- Example: You open Outlook → Emails come to your computer → Not available on phone.
IMAP – Internet Message Access Protocol
- Main job: Sync emails between the server and all your devices.
- What happens: Emails stay on the server, so you can read them on phone, laptop, or tablet and see the same messages everywhere.
- Ports: 143 (basic), 993 (secure).
- Example: You read an email on your phone → It shows as read on your computer too.
POP3 vs IMAP (Simple Difference)
- POP3: Download and keep on one device (like taking letters from the post office and keeping them at home).
- IMAP: Sync and keep on the server (like leaving letters in the post office, but you can read them from anywhere).
Easy Comparison Table
| Protocol | Main Job | Secure Port | Where Emails are Stored | Works on Many Devices? |
|---|---|---|---|---|
| SMTP | Push (send) emails | 587, 465 | Not for storage | No |
| POP3 | Download emails | 995 | Only on your device | No |
| IMAP | Sync emails | 993 | On the server | Yes |
- Key Phrase: “IMAP syncs emails; POP3 downloads locally.”
- Common Question: POP3 vs IMAP? (Answer: IMAP for multi-device, POP3 for single-device).
- Stand Out: Mention TLS/SSL and MX records.
Quick Reference Table
| Protocol | Purpose | Port (Secure) | Security |
|---|---|---|---|
| HTTP | Web communication | 80 | None |
| HTTPS | Secure web communication | 443 | SSL/TLS |
| FTP | File transfer | 21, 20 | FTPS/SFTP |
| DNS | Domain to IP resolution | 53 | DNSSEC |
| DHCP | Dynamic IP assignment | 67, 68 | None |
| SMTP | Send email | 587, 465 | TLS/SSL |
| POP3 | Retrieve email (download) | 995 | SSL/TLS |
| IMAP | Retrieve email (sync) | 993 | SSL/TLS |
Interview Strategies
- Be Concise: Explain protocols in 1-2 sentences, elaborate if asked.
- Use Examples:
- HTTP: Fetching a webpage.
- HTTPS: Online banking.
- DNS: Resolving google.com.
- DHCP: Connecting to Wi-Fi.
- SMTP: Sending an email.
- Highlight Security:
- HTTPS uses SSL/TLS.
- SFTP over FTP.
- DNSSEC for DNS.
- TLS for email protocols.
- Know Processes:
- DNS resolution steps.
- DHCP DORA process.
- HTTP request-response cycle.
- Practice Questions:
- Explain HTTP vs HTTPS.
- What are idempotent methods?
- Why is 404 different from 403?
- How does DNS resolve a domain?
- What’s the DORA process in DHCP?
- Why use IMAP over POP3?
Sample Interview Q&A
Q: Explain HTTP vs HTTPS.
Answer: HTTP transfers web data in plain text over port 80, while HTTPS uses SSL/TLS encryption over port 443 for security. HTTPS ensures confidentiality, integrity, and authentication, ideal for sensitive data like logins or payments. Example: https://www.paypal.com for secure transactions.
Q: What’s the difference between GET and POST?
Answer: GET retrieves data, is safe and idempotent, with parameters in the URL (e.g., GET /search?q=book). POST sends data in the body to create/update resources, is not idempotent, used for forms or APIs (e.g., POST /users with JSON).
Q: How does DNS work?
Answer: DNS resolves domain names to IPs. The client checks cache, then a recursive resolver queries root servers, TLD servers, and authoritative servers to get the IP. Example: www.google.com resolves to 142.250.190.78, cached for speed.